8 October 2016
In report ‘Cybersecurity is just too much trouble for the general public, claims study’ published on 6 October at the Tripwire state-of-security blog, Graham Cluley cites from the NIST study Security Fatigue:
“Participants expressed a sense of resignation, loss of control, fatalism, risk minimization, and decision avoidance, all characteristics of security fatigue. The authors found that the security fatigue users experience contributes to their cost-benefit analyses in how to incorporate security practices and reinforces their ideas of lack of benefit for following security advice.”
We should not be surprised ‘that the public is suffering from “security fatigue” and a feeling of helplessness when it comes to their online security’. Most of the advice for end users in the information security domain is just puzzling. Let me make this clear with an example.
Renowned German Stiftung Warentest assessed 15 e-mail providers in the October 2016 edition of the Test magazine. Focus of the assessment was data privacy, ‘the protection of customers and emails against unwanted looks’. And, of course, usability. Table 1 below shows the Stiftung Warentest quality ranking.
| Provider |
Quality Ranking (1) |
| Mailbox.org Tarif Mail |
1.4 |
| Posteo |
1.4 |
| Mail.de Plusmail |
2.2 |
| GMX Topmail |
2.3 |
| Web.de Club |
2.3 |
| Web.de Freemail |
2.5 |
| GMX Freemail |
2.6 |
| Telekom Freemail |
2.6 |
| Freenetmail Basic |
2.7 |
| Telekom Mail / Cloud M |
2.7 |
| 1&1 Mail Basic |
3.1 |
| AOL Mail |
3.1 |
| Yahoo Mail |
3.2 |
| Microsoft Outlook.com |
3.3 |
| Google Gmail |
3.4 |
Table 1: Stiftung Warentest rankings
(1) Quality Ranking: 0.5 .. 1.5: Very good, 1.6 .. 2.5: Good, 2.6 .. 3.5: Average
At a first glance, the table suggests that it is sufficient to use one of these providers (all were rated from very good to average) and security is guaranteed.
Unfortunately, this assessment is very misleading. Email encryption is just one aspect of information security. It protects against cyber criminals, state-sponsored attackers or insider attacks because the information is not readable unless the attacker has access to the encryption key.
If an attacker is able to compromise a user’s account, e.g. through a password phishing attack, he might have full access to all emails, although they are encrypted.
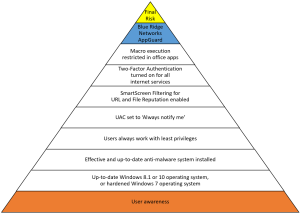
To secure an account against phishing with frequent password changes and the use of individual passwords for different services, is not sufficient. And usability is bad, even if password managers are used. Two-Factor Authentication (TFA) or one-time passwords are the tools of choice to enhance security against phishing attacks.
Table 2 shows the Stiftung Warentest results updated with details about TFA availability.
| Provider |
Quality Ranking (1) |
TFA available |
With soft token |
With SMS |
With hard token |
| Mailbox.org Tarif Mail |
1.4 (2) |
Yes |
Yes |
|
Yes |
| Posteo |
1.4 |
Yes |
Yes |
|
|
| Mail.de Plusmail |
2.2 |
Yes |
Yes |
|
Yes |
| GMX Topmail |
2.3 |
No |
|
|
|
| Web.de Club |
2.3 |
No |
|
|
|
| Web.de Freemail |
2.5 |
No |
|
|
|
| GMX Freemail |
2.6 |
No |
|
|
|
| Telekom Freemail |
2.6 |
No |
|
|
|
| Freenetmail Basic |
2.7 |
No |
|
|
|
| Telekom Mail / Cloud M |
2.7 |
No |
|
|
|
| 1&1 Mail Basic |
3.1 |
Undef. (2) |
|
|
|
| AOL Mail |
3.1 |
Yes |
|
Yes |
|
| Yahoo Mail |
3.2 |
Yes |
|
Yes |
|
| Microsoft Outlook.com |
3.3 |
Yes |
Yes |
Yes |
|
| Google Gmail |
3.4 |
Yes |
Yes |
Yes |
Yes |
Table 2: Rankings updated with details about TFA
(1) Quality Ranking: 0.5 .. 1.5: Very good, 1.6 .. 2.5: Good, 2.6 .. 3.5: Average
(2) It was not possible to determine whether TFA is available from the provider’s homepage
Only 7 of the 15 email providers allow the use of a second factor. The limitation to one aspect of information security creates puzzling results and a false sense of security. It is therefore no wonder that consumers show the ‘characteristics of security fatigue’.
TFA with soft tokens is under normal conditions activated within seconds, and very easy to use. From my point of view, service providers should create the needed attention and force the use of TFA. It is not sufficient to notify the users of new waves of phishing attacks.
Have a good weekend.