1 April 2017
Keep your software patched and defend against social engineering, and you will win the battle against the bad guys. Let me be clear: From my point of view this is simply not enough. Nevertheless, Roger A. Grimes’ post “Vastly improve your IT security in 2 easy steps” published on March 21, 2017 at InfoWorld is really worth reading, in particular the section about patching.
The key to diminishing this risk is to identify the right software to patch and do it really, really well. The risk reducers I respect know the difference between the largest unpatched program in their environment and the unpatched program mostly likely to be exploited in their environment. A security expert knows there is usually a gulf between the two.
In particular in the production domain, where patching has always to be delayed to the next scheduled maintenance, this is a very important hint.
The big question is: How can we identify the right software on the right and important systems? Without an up-to-date asset directory with the relevant details about cyber security this is a very complex and expensive matter.
But even with an up-to-date asset directory this remains a complex task.
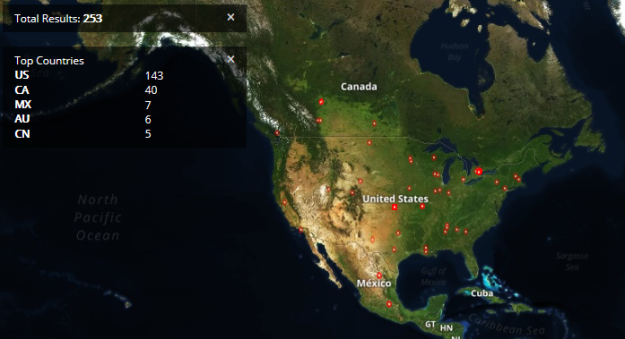
Rockwell/Allen Bradley Systems directly connected to the Internet in North America
For example, the likelihood of a cyber-attack on an Industrial Control System (ICS), which is directly connected to the internet, is many times higher than the likelihood of an attack on an ICS which is completely isolated in a security zone within the production network. The first ICS is definitely one of those systems Roger Grimes has in mind, the latter can be ignored.
But the likelihood of a cyber-attack is only half the story. For example, in functional safety the risk is the combination of the probability that a hazard will lead to an accident and the likely severity of the accident if it occurs. Thus, from this point of view, even the first ICS may be uncritical unless it is not used for controlling a critical infrastructure.
To identify the right and important systems is the hard task. It requires an up-to-date asset inventory and a smart risk management process. The plain patching process is just a piece of cake.
Have a good weekend.

