28 May 2017
Actually, it was only a matter of time until Samba, the popular implementation of the Windows SMB services on Linux and Unix, was hit by a WannyCry akin malware. All version of Samba from 3.5.0 onwards are vulnerable to CVE-2017-7494 or SambaCry.
The good news is that this vulnerability is complex to exploit: An attacker must upload a shared library with the malicious code to a writable samba share and then cause the server to load and execute it. Patches are available for the major Linux distributions.
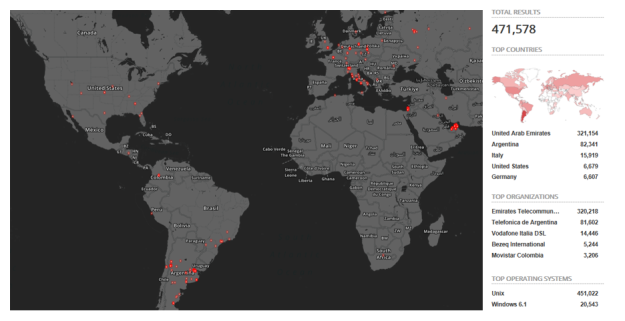
How large is the problem? Shodan finds 471,578 systems which are exposed to the Internet.
90% of the systems are operated in 3 countries, United Arab Emirates, Argentina, and Italy by the major telecommunication providers in these countries. Since an older version of Samba is used on this internet routers they are not vulnerable against SambaCry.
Most of the work has to be done in the United States and Germany. Although only 2 % of the affected systems are operated there, many organizations are affected.
Don’t panic! Even though many systems are affected by SambaCry this does not mean, that they are vulnerable against the exploit. Remember, you have to upload the malicious code to a writable Samba share on a server first. Under normal conditions, Linux admins don’t open Samba shares writable to everyone on servers exposed to the internet.
Thus, the best approach to reduce the risk is to check the Linux systems at the network perimeter with publicly available Samba shares and to close the writable, if any. As always, it is good to have an up-to-date system inventory in place. This will reduce the amount of work dramatically.
Take care! And don’t forget to check the network perimeter to your production networks.