19 August 2018
Mohit Kumar’s report on DeepLocker (1) published on 9 August 2018 in The Hacker News made me jump. Is AI becoming the doomsday machine of the 21st century?
DeepLocker is the result of a study (2) performed by IBM Researcher Marc Stoecklin and his colleagues on the question how the use of AI will change cyber-attacks:
“DeepLocker has changed the game of malware evasion by taking a fundamentally different approach from any other current evasive and targeted malware.”
The good news is that DeepLocker still needs a carrier app. Marc Stoecklin writes:
“DeepLocker hides its malicious payload in benign carrier applications, such as a video conference software, to avoid detection by most antivirus and malware scanners.”
DeepLocker is hence not invincible. A compromised carrier app will have another fingerprint than the not compromised version, at least until the carrier app is not compromised during development.
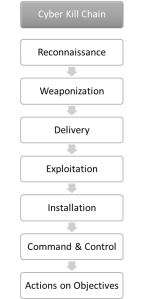
With this, program reputation, a must-have in every Next Generation Endpoint Protection Solution (NGEPS), can stop a malicious app very early in the Cyber Kill Chain (CKC).
The bad news is that reverse engineering is hardly possible. Marc Stoecklin writes:
“What is unique about DeepLocker is that the use of AI makes the “trigger conditions” to unlock the attack almost impossible to reverse engineer. The malicious payload will only be unlocked if the intended target is reached. It achieves this by using a deep neural network (DNN) AI model.”
Although I am fond of reading malware analysis papers I won’t miss them. From my point of view, it is only important that the NGEPS blocks the payload from being executed. In terms of the Cyber Kill Chain this means: ideally in the delivery phase, the latest in the installation phase.
For more details on DeepLocker please see the presentation (3) Marc Stoecklin delivered at the Black Hat 2018 conference.
Don’t panic, but be prepared: Skynet will gain world supremacy soon …
Have a great week.
- Kumar M. Researchers Developed Artificial Intelligence-Powered Stealthy Malware [Internet]. The Hacker News. 2018 [cited 2018 Aug 13]. Available from: https://thehackernews.com/2018/08/artificial-intelligence-malware.html
- Stoecklin MP. DeepLocker: How AI Can Power a Stealthy New Breed of Malware [Internet]. Security Intelligence. 2018 [cited 2018 Aug 13]. Available from: https://securityintelligence.com/deeplocker-how-ai-can-power-a-stealthy-new-breed-of-malware/
- Stoecklin MP, Kirat D, Jang J. DeepLocker – Concealing Targeted Attacks with AI Locksmithing [Internet]. Black Hat USA 2018. 2018 [cited 2018 Aug 19]. Available from: https://www.blackhat.com/us-18/briefings/schedule/#deeplocker—concealing-targeted-attacks-with-ai-locksmithing-11549