6. Mai 2021
Nach der kurzen Einführung in die Theorie von RoSI nun ein Praxisbeispiel.
Szenario
Ein Unternehmen betreibt an 2 Standorten prozesstechnische Anlagen. Jede Anlage besteht aus 5 Teilanlagen. Insgesamt werden pro Standort 100 Workstations und 20 Server betrieben. Die Standorte sollen im Rahmen eines Digitalisierungsprojektes enger mit der Forschungs- Entwicklungsabteilung sowie den Produktionsplanungssystemen und der Office-Cloud vernetzt werden. Vorab führt das Produktionsmanagement eine Risikoanalyse durch.
Die Risikoanalyse ermittelt ein hohes Risiko in Bezug auf eine Malware-Infektion, die zu einem Stillstand an beiden Standorten führen könnte. Der Produktionsmanager schätzt, dass eine Infektion mit Ransomware im ungünstigsten Fall zu einem Produktionsausfall von 5 Tagen führen könnte. Ein Tag Produktionsausfall kostet das Unternehmen 200T€.
Die Geschäftsleitung macht klar, dass unter der geschätzten Auslastung für die nächsten 36 Monate ein Ausfall von max. 1,5 Tagen pro Jahr akzeptabel ist. Das ermittelte Risiko ist nicht akzeptabel ist. Die OT-Security erhält die Aufgabe, die wirtschaftlich beste Lösung zur Reduktion des Risikos um 70% (von 1Mio. € auf 300T€) zu ermitteln.
Damit sind die Randbedingungen für die RoSI-Betrachtung festgelegt:
KE: Die Kosten des Sicherheitsereignisses KE belaufen sich auf KE = 1 Mio. €.
SR%: Sicherheitsmaßnahme S soll das Risiko um SR% = 70% reduzieren.
KES: Die Kosten des Sicherheitsereignisses sollen reduziert werden auf KES <= 300T€
Design der Maßnahmen
Das Unternehmen setzt in der Produktion noch keine Antimalware-Lösung ein. Zur Risikoreduzierung werden 3 traditionelle Ansätze verfolgt, die auf Sicherheitslösungen beruhen, die vom Hersteller der Automatisierungslösung freigegeben sind.
Alt1: Antimalware-Lösung McAfee Endpoint Protection
Alt2: Antimalware-Lösung McAfee Endpoint Protection plus Microsoft AppLocker
Alt3: Antimalware-Lösung McAfee Endpoint Protection plus McAfee Application Control
Microsoft AppLocker ist eine Application-Directory-Allow-Listing-Lösung, die von vielen Herstellern von Automatisierungslösungen zur Grundhärtung der Systeme empfohlen wird. AppLocker ist seit Windows 7 in der Enterprise-Version des Betriebssystems verfügbar. McAfee Application Control ist eine system-basierte Application-Whitelisting-Lösung, die von vielen Herstellern von Automatisierungslösungen zum Schutz vor bekannter und neuer Malware empfohlen wird. Sie kann auch Crypto-Würmer wie WannaCry und NotPetya, die sich im Systemkontext von System zu System bewegen, abwehren.
Bewertung der Effektivität der Lösungsansätze
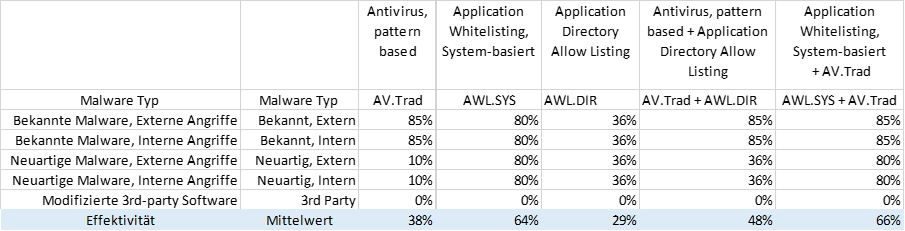
IT- und OT-Security führen eine Bewertung der Effektivität der verschiedenen systemtechnischen Ansätze durch. Daraus ergibt sich folgendes Bild:
Die klassische Antimalware-Lösung „pattern-based Antivirus“ hat mit 38% eine unzureichende Schutzwirkung, ebenso wie die Lösung „Application Directory Allow Listing“ und die Kombination aus AV.Trad und AWL.DIR.
Die „system-basierte Application-Whitelisting-Lösung“ kommt bereits sehr nahe (64%) an die geforderte Risikoreduzierung SR% = 70% heran.
Die Kombination aus AV.Trad und AWL.SYS kommt am nächsten an die geforderte Risikoreduzierung von 70% heran.
Die Details zur Bewertung stehen hier bereit.
Kostenbetrachtung
Die Kosten aller Lösungen wurden untersucht. Lizenz- und Betriebskosten wurden über einen Zeitraum von 3 Jahren betrachtet. Die Kosten für die Erstinstallation wurden berücksichtigt. Bei den Lizenzkosten wurden Lizenzstaffeln (101-250 Workstations und 26-50 Server) berücksichtigt. Preise wurden per Internet-Recherche ermittelt. Das Kostenmodell steht hier zum Download verfügbar.
RoSI
Die Berechnung von RoSI über 3 Jahre ergibt folgendes Bild:
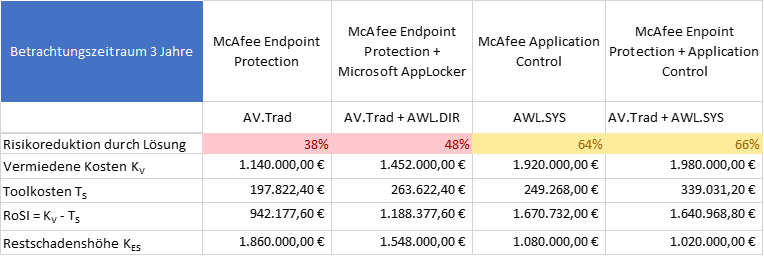
Alle Lösungen haben ein positives RoSI. Die Optionen Alt1: AV.Trad und Alt2: AV.Trad + AWL-DIR scheiden aus, da das Restrisiko KES deutlich höher ist als die geforderten 900T€

Alternative Alt3: Antimalware-Lösung McAfee Endpoint Protection plus McAfee Application Control und McAfee Application Control führen zu einer ähnlichen Risikoreduktion. Alt3 hat jedoch deutlich höhere Kosten.
Für welche Lösung wird sich die Produktionsleitung entscheiden?
Dies ist der letzte Post aus der Ransomware/RoSI-Reihe. Mehr zu RoSI gibt es beim IMI Virtuellen Dialog „Costs and Benefits of Security“ am 11.05.2021. Neben praktischen Anwendungsbeispielen von ABB und Fortinet erweitere ich diese Analyse um eine moderne EDR-Lösung.
Viel Erfolg mit RoSI!